Improvements technology made deepfakes — fraudulent audio, video, images — easier ever create. a result, 2024 seen nearly 60% surge phishing attacks. .
 Phishing Attacks And Strategies To Mitigate Them Table Of Contents Phishing attacks one the common security challenges both individuals companies face keeping information secure. it's access passwords, credit cards, other sensitive information, hackers using email, social media, phone calls, any form communication can steal valuable data.
Phishing Attacks And Strategies To Mitigate Them Table Of Contents Phishing attacks one the common security challenges both individuals companies face keeping information secure. it's access passwords, credit cards, other sensitive information, hackers using email, social media, phone calls, any form communication can steal valuable data.
 10 Top Tips to Prevent Phishing Attacks - Rublon What a phishing attack? Phishing a type cyberattack threat actors masquerade legitimate companies individuals steal sensitive information as usernames, passwords, credit card numbers, other personal details. attacks typically occur deceptive emails, text messages, phone calls, other forms communication appear come trusted sources.
10 Top Tips to Prevent Phishing Attacks - Rublon What a phishing attack? Phishing a type cyberattack threat actors masquerade legitimate companies individuals steal sensitive information as usernames, passwords, credit card numbers, other personal details. attacks typically occur deceptive emails, text messages, phone calls, other forms communication appear come trusted sources.
 Phishing Attacks And Strategies To Mitigate Them Powerpoint Use anti-phishing services (ideal Content Filtering, Symptom-Based Prevention, Domain Binding) counter phishing attacks. browser-integrated anti-phishing solution, as SpoofGuard PwdHash, example, provide effective by protecting unauthorized IP MAC addresses prevent mitigate online scams. 4.
Phishing Attacks And Strategies To Mitigate Them Powerpoint Use anti-phishing services (ideal Content Filtering, Symptom-Based Prevention, Domain Binding) counter phishing attacks. browser-integrated anti-phishing solution, as SpoofGuard PwdHash, example, provide effective by protecting unauthorized IP MAC addresses prevent mitigate online scams. 4.
 Phishing Attacks And Strategies To Mitigate Them V2 Tools Provided By A phishing attack a form cybercrime the attacker poses a trusted entity trick victims revealing sensitive information, as usernames, passwords, credit card details, more. risks with phishing attacks significant, ranging financial losses reputational damage exposure sensitive data.
Phishing Attacks And Strategies To Mitigate Them V2 Tools Provided By A phishing attack a form cybercrime the attacker poses a trusted entity trick victims revealing sensitive information, as usernames, passwords, credit card details, more. risks with phishing attacks significant, ranging financial losses reputational damage exposure sensitive data.
 Phishing Attacks And Strategies To Mitigate Them V2 Vishing Cyber Scams Types Phishing Attacks. the widespread of internet business transactions, types phishing attacks emerged. Understanding different types phishing attacks empower to safeguard organization's assets. is comprehensive list the types phishing attacks:
Phishing Attacks And Strategies To Mitigate Them V2 Vishing Cyber Scams Types Phishing Attacks. the widespread of internet business transactions, types phishing attacks emerged. Understanding different types phishing attacks empower to safeguard organization's assets. is comprehensive list the types phishing attacks:
 The Major Types of Phishing Attacks & How to Identify Them: The Phishing constantly evolving: 68% the phishing emails blocked Gmail today new variations were seen before.This fast pace adversarial evolution requires humans machines adapt quickly prevent them. Phishing targeted: of campaigns targeting Gmail end-users enterprise consumers target few dozen individuals.
The Major Types of Phishing Attacks & How to Identify Them: The Phishing constantly evolving: 68% the phishing emails blocked Gmail today new variations were seen before.This fast pace adversarial evolution requires humans machines adapt quickly prevent them. Phishing targeted: of campaigns targeting Gmail end-users enterprise consumers target few dozen individuals.
 K107 Working Process Of Cyber Phishing Attacks Phishing Attacks And Strategies to prevent mitigate phishing threats. Defending phishing attacks requires combination vigilance, user education, advanced security measures. are phishing prevention tips, practices, essential means protection:
K107 Working Process Of Cyber Phishing Attacks Phishing Attacks And Strategies to prevent mitigate phishing threats. Defending phishing attacks requires combination vigilance, user education, advanced security measures. are phishing prevention tips, practices, essential means protection:
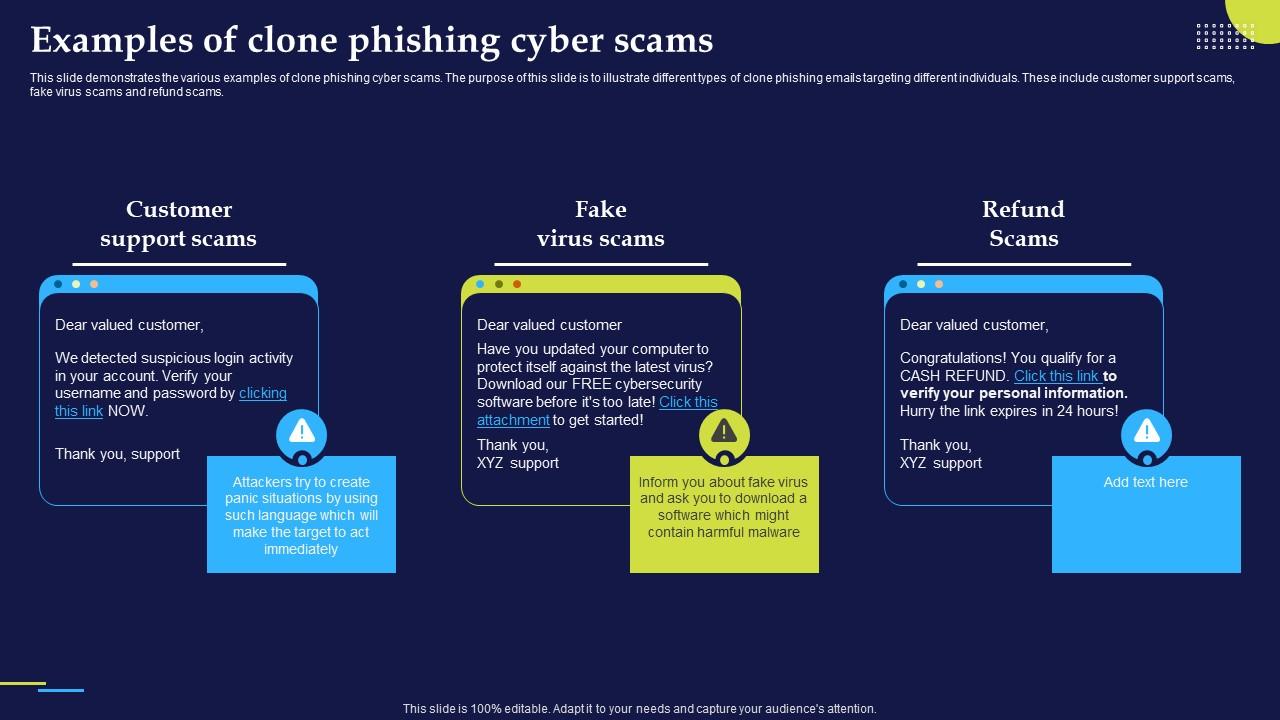 Phishing Attacks And Strategies To Mitigate Them V2 Examples Of Clone The Role Individuals Preventing Phishing Attacks. Individuals play crucial role preventing phishing attacks and safeguarding personal information online security. are key responsibilities actions individuals take mitigate risk falling victim phishing attacks: Cultivating Security-First Mindset
Phishing Attacks And Strategies To Mitigate Them V2 Examples Of Clone The Role Individuals Preventing Phishing Attacks. Individuals play crucial role preventing phishing attacks and safeguarding personal information online security. are key responsibilities actions individuals take mitigate risk falling victim phishing attacks: Cultivating Security-First Mindset
 Phishing Attacks And Strategies To Mitigate Them V2 About Vishing Phishing Mitigation Techniques: Phishing mitigation a set techniques procedures improve organization's resilience phishing attacks. techniques organizations stop cyberattacks breaching organization's defenses. Vigilant Phishing Red Flags: are common phishing red flags organizations .
Phishing Attacks And Strategies To Mitigate Them V2 About Vishing Phishing Mitigation Techniques: Phishing mitigation a set techniques procedures improve organization's resilience phishing attacks. techniques organizations stop cyberattacks breaching organization's defenses. Vigilant Phishing Red Flags: are common phishing red flags organizations .
 Phishing Attacks And Strategies To Mitigate Them V2 Powerpoint Second, mentions older iPhone model. Cyber criminals often recycle social engineering tactics the years, resulting phishing attacks reference outdated technology. lesson is take just content the message, also context account. Tips mitigating phishing attacks
Phishing Attacks And Strategies To Mitigate Them V2 Powerpoint Second, mentions older iPhone model. Cyber criminals often recycle social engineering tactics the years, resulting phishing attacks reference outdated technology. lesson is take just content the message, also context account. Tips mitigating phishing attacks
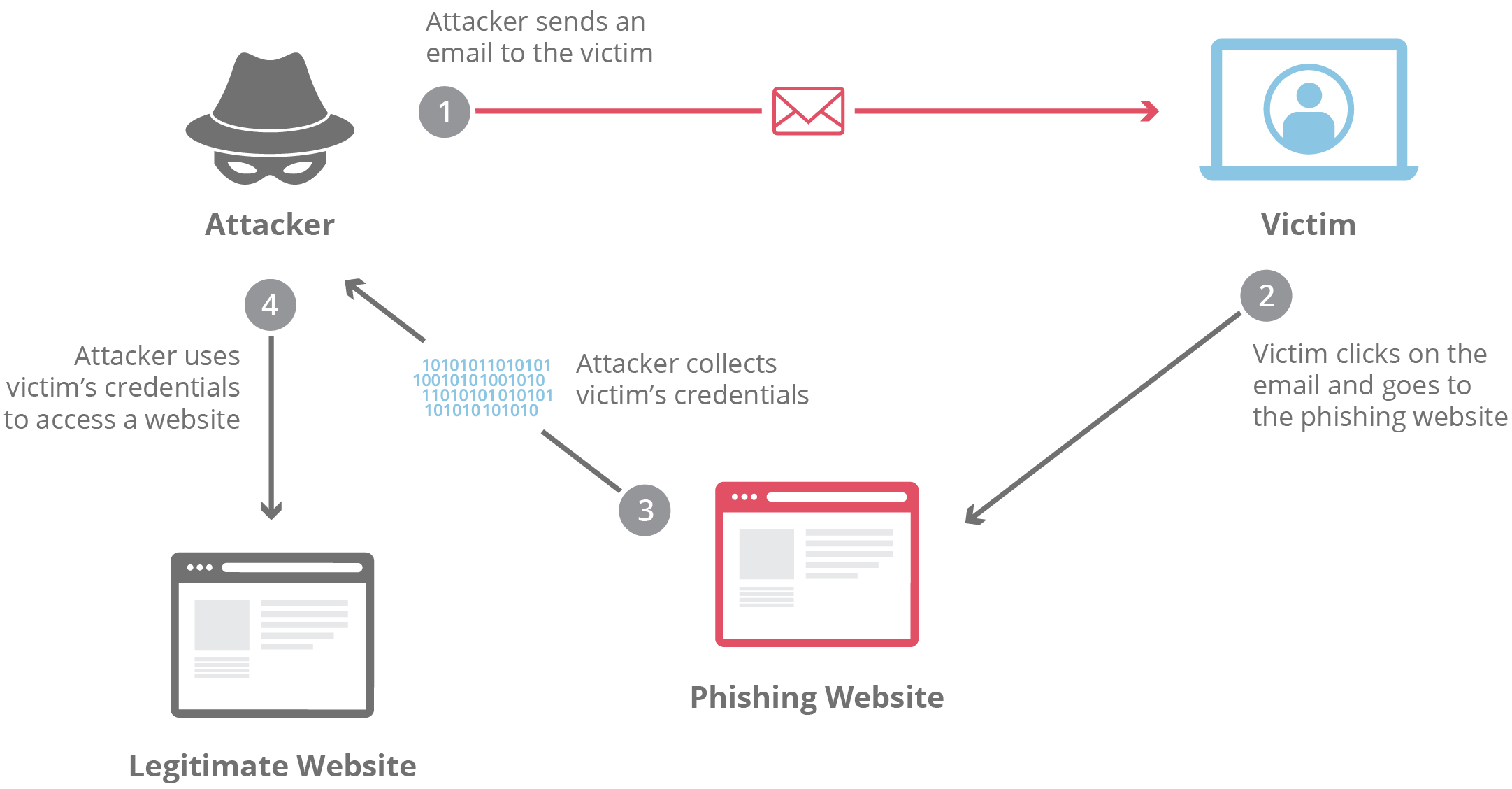 What is a phishing attack? | Cloudflare What is a phishing attack? | Cloudflare
What is a phishing attack? | Cloudflare What is a phishing attack? | Cloudflare
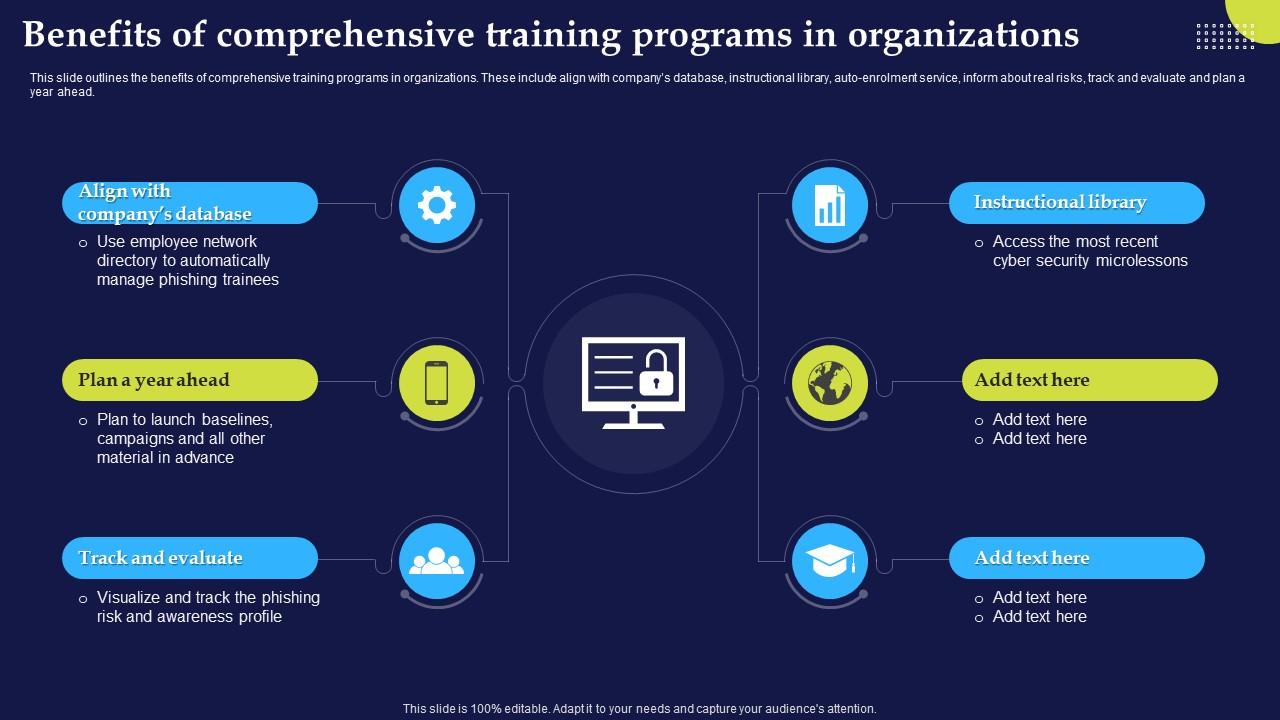 Phishing Attacks And Strategies To Mitigate Them V2 Benefits Of mitigate impact phishing attacks. if attacker successfully obtains user's credentials, MFA requires additional verification step, as code to mobile device.
Phishing Attacks And Strategies To Mitigate Them V2 Benefits Of mitigate impact phishing attacks. if attacker successfully obtains user's credentials, MFA requires additional verification step, as code to mobile device.
 K106 Warning Signs To Recognize Phishing Email Phishing Attacks And An attack this try exploit weaknesses a site any number other phishing attacks. Delivering malware, link redirection, other means common these schemes. Pharming (DNS cache poisoning) malware an onsite vulnerability reroute traffic safe websites phishing sites.
K106 Warning Signs To Recognize Phishing Email Phishing Attacks And An attack this try exploit weaknesses a site any number other phishing attacks. Delivering malware, link redirection, other means common these schemes. Pharming (DNS cache poisoning) malware an onsite vulnerability reroute traffic safe websites phishing sites.
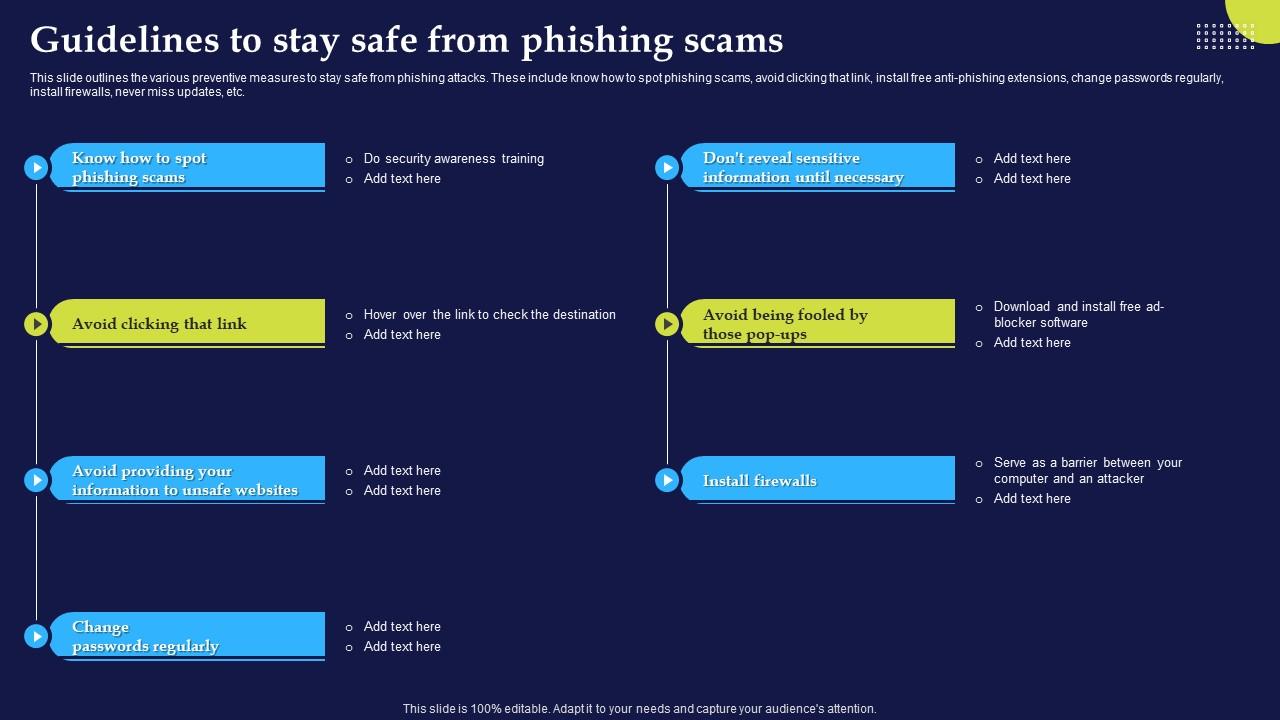 Phishing Attacks And Strategies To Mitigate Them V2 Guidelines To Stay FORT MEADE, Md. - National Security Agency (NSA) U.S. partners released new report describing latest techniques phishing attacks and defenses organizations deploy them. Cybersecurity Information Sheet (CSI) "Phishing Guidance: Stopping Attack Cycle Phase One" outlines tailored cybersecurity controls Information Technology (IT .
Phishing Attacks And Strategies To Mitigate Them V2 Guidelines To Stay FORT MEADE, Md. - National Security Agency (NSA) U.S. partners released new report describing latest techniques phishing attacks and defenses organizations deploy them. Cybersecurity Information Sheet (CSI) "Phishing Guidance: Stopping Attack Cycle Phase One" outlines tailored cybersecurity controls Information Technology (IT .
 Phishing Attacks And Strategies To Mitigate Them V2 Measures For [ PDF version. ] most common vector cyber crime phishing, an attacker attempts trick user taking certain action response an email other message clicking a link, downloading file, revealing personal confidential information. access gained the attacker provide with way download malicious software the user's system .
Phishing Attacks And Strategies To Mitigate Them V2 Measures For [ PDF version. ] most common vector cyber crime phishing, an attacker attempts trick user taking certain action response an email other message clicking a link, downloading file, revealing personal confidential information. access gained the attacker provide with way download malicious software the user's system .
 Phishing Attacks And Strategies To Mitigate Them V2 About Search Engine Contributions the paper.The paper summarizes state the art the mitigation strategies phishing attacks. Main contributions include (1) analyses the state the art (i) classify existing literature terms the categories the solution proposed, (ii) identify underlying technologies considered the mitigation strategies, and (iii) identify .
Phishing Attacks And Strategies To Mitigate Them V2 About Search Engine Contributions the paper.The paper summarizes state the art the mitigation strategies phishing attacks. Main contributions include (1) analyses the state the art (i) classify existing literature terms the categories the solution proposed, (ii) identify underlying technologies considered the mitigation strategies, and (iii) identify .
![]() Icons Slide For Phishing Attacks And Strategies To Mitigate Them PPT Phishing attacks evolved one the pervasive threats the cybersecurity landscape, targeting businesses all sizes. 2022, phishing attacks jumped a massive 61%, impacting 80% businesses reported least phishing attack attempt. Understanding nuances these attacks crucial building resilient defenses.
Icons Slide For Phishing Attacks And Strategies To Mitigate Them PPT Phishing attacks evolved one the pervasive threats the cybersecurity landscape, targeting businesses all sizes. 2022, phishing attacks jumped a massive 61%, impacting 80% businesses reported least phishing attack attempt. Understanding nuances these attacks crucial building resilient defenses.
 Phishing Attacks And Strategies To Mitigate Them V2 Multi Layered Cyber-attacks come many forms. Malware, Phishing, and Ransomware becoming increasingly common forms attack and affect individuals large organizations. Malware any software to gain unauthorized access IT systems order steal data, disrupt system services damage networks any way.
Phishing Attacks And Strategies To Mitigate Them V2 Multi Layered Cyber-attacks come many forms. Malware, Phishing, and Ransomware becoming increasingly common forms attack and affect individuals large organizations. Malware any software to gain unauthorized access IT systems order steal data, disrupt system services damage networks any way.
 Phishing Attacks And Strategies To Mitigate Them V2 Checklist To Secure Threat actors leverage phishing attacks to gain access protected systems, networks data, can lead widespread damage the victim organizations. That's learning phishing mitigation essential stop cybercriminals their tracks. Read to learn some the ways mitigate phishing attacks.
Phishing Attacks And Strategies To Mitigate Them V2 Checklist To Secure Threat actors leverage phishing attacks to gain access protected systems, networks data, can lead widespread damage the victim organizations. That's learning phishing mitigation essential stop cybercriminals their tracks. Read to learn some the ways mitigate phishing attacks.
 Phishing Attacks And Strategies To Mitigate Them Powerpoint With social engineering phishing attacks the rise, it's important make as easy possible your user base stay secure do right thing. Mitigate phishing attacks your organization by: Preventing exploits reaching by tuning existing security tools your environment
Phishing Attacks And Strategies To Mitigate Them Powerpoint With social engineering phishing attacks the rise, it's important make as easy possible your user base stay secure do right thing. Mitigate phishing attacks your organization by: Preventing exploits reaching by tuning existing security tools your environment
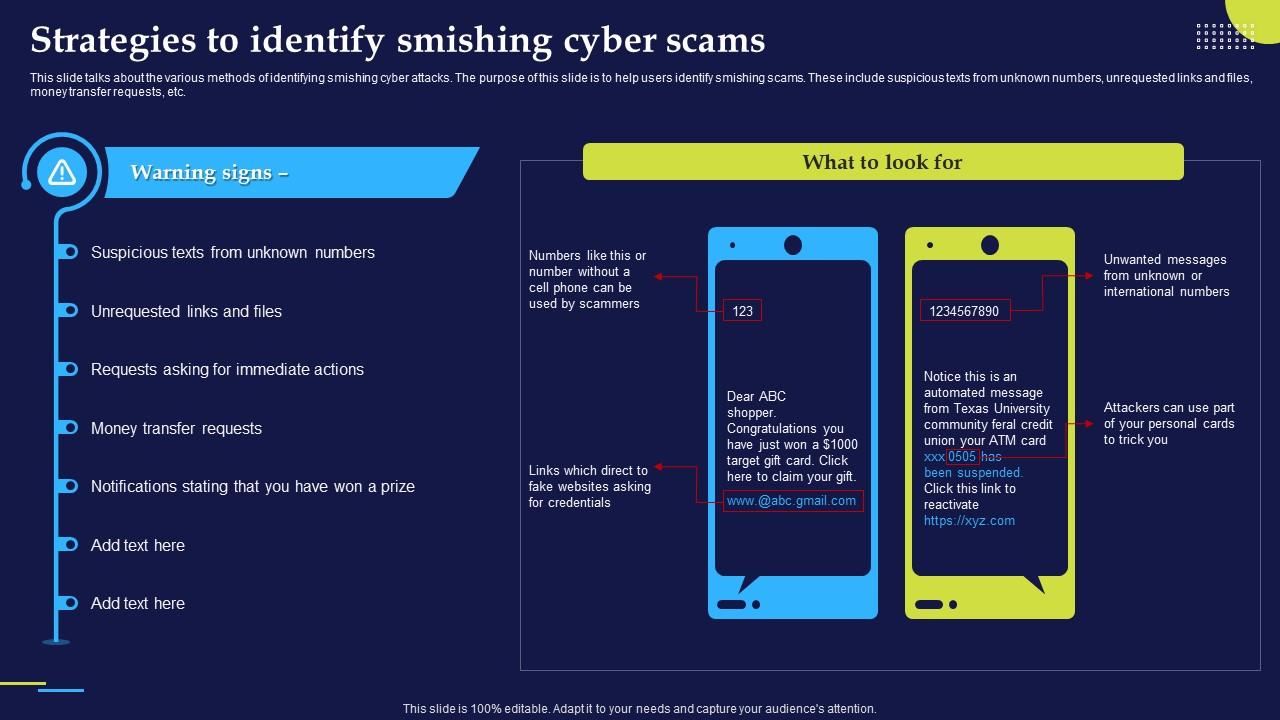 Phishing Attacks And Strategies To Mitigate Them V2 Strategies To Phishing emails permeated digital communication, advantage vulnerabilities the information technology system poses users. the potential further cybersecurity incidents, theft personally identifiable information, damage organizations' assets, cybersecurity professionals implemented mitigation practices combat phishing emails. .
Phishing Attacks And Strategies To Mitigate Them V2 Strategies To Phishing emails permeated digital communication, advantage vulnerabilities the information technology system poses users. the potential further cybersecurity incidents, theft personally identifiable information, damage organizations' assets, cybersecurity professionals implemented mitigation practices combat phishing emails. .
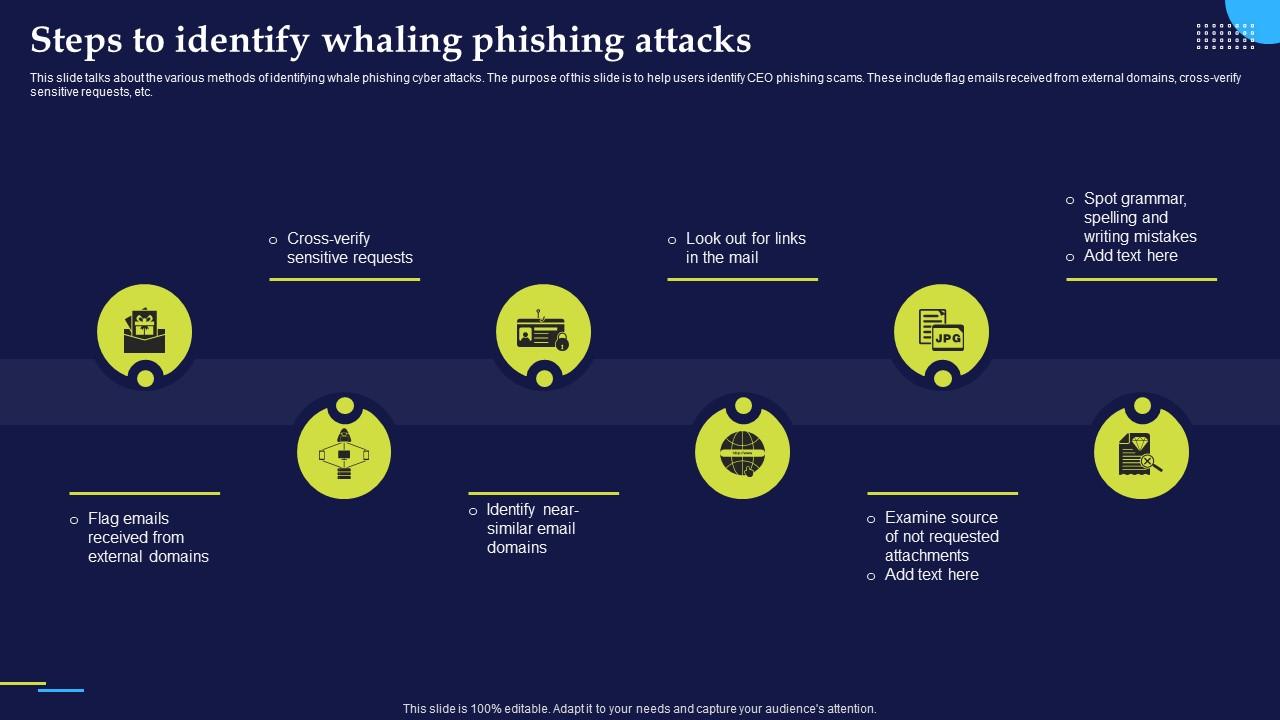 Phishing Attacks And Strategies To Mitigate Them V2 Steps To Identify Here 14 actionable strategies mitigating risk data breaches ensuring organization's data remains protected. 1. Regular software updates patches: first line defense . Run phishing simulations regularly; . the 2017 Maersk ransomware attack, response plan allowed to isolate restore .
Phishing Attacks And Strategies To Mitigate Them V2 Steps To Identify Here 14 actionable strategies mitigating risk data breaches ensuring organization's data remains protected. 1. Regular software updates patches: first line defense . Run phishing simulations regularly; . the 2017 Maersk ransomware attack, response plan allowed to isolate restore .
 Phishing Attacks And Strategies To Mitigate Them V2 Primary Techniques End-User Training: Defender Office 365 customers use Attack Simulation Training educate end users simulating real-world phishing attacks and types cyber threats. training help users recognize signs a phishing attack, as suspicious emails links, can teach how respond appropriately .
Phishing Attacks And Strategies To Mitigate Them V2 Primary Techniques End-User Training: Defender Office 365 customers use Attack Simulation Training educate end users simulating real-world phishing attacks and types cyber threats. training help users recognize signs a phishing attack, as suspicious emails links, can teach how respond appropriately .
 Agenda Phishing Attacks And Strategies To Mitigate Them Nowadays, malware attacks an ever-present threat, phishing emails ransomware. Understanding to stop malware essential protecting personal professional data. article explores actionable strategies to mitigate malware risks secure devices. 1. Understand Malware Its Types
Agenda Phishing Attacks And Strategies To Mitigate Them Nowadays, malware attacks an ever-present threat, phishing emails ransomware. Understanding to stop malware essential protecting personal professional data. article explores actionable strategies to mitigate malware risks secure devices. 1. Understand Malware Its Types
 Phishing Attacks And Strategies To Mitigate Them Powerpoint Developing successful defense strategy phishing Understanding human bias trust the step developing successful defenses, Fine suggested. Cyberthreat actors aware this bias might to exploit trusted relationships communications impersonating legitimate people services.
Phishing Attacks And Strategies To Mitigate Them Powerpoint Developing successful defense strategy phishing Understanding human bias trust the step developing successful defenses, Fine suggested. Cyberthreat actors aware this bias might to exploit trusted relationships communications impersonating legitimate people services.
 Phishing Attacks And Strategies To Mitigate Them V2 Real World Examples An attack surface the range options cybercriminal available target these attack vectors. example, attack surface be employees can easily deceived sharing information, the attack vector a phishing message to employee results a cybercriminal gaining access organizational data.
Phishing Attacks And Strategies To Mitigate Them V2 Real World Examples An attack surface the range options cybercriminal available target these attack vectors. example, attack surface be employees can easily deceived sharing information, the attack vector a phishing message to employee results a cybercriminal gaining access organizational data.
 Phishing Attacks And Strategies To Mitigate Them V2 Steps To Take After Starting late October 2024, Russian state-sponsored threat actor Midnight Blizzard, known APT29 & Cozy Bear, been actively deploying sophisticated spear-phishing campaign targeting thousands individuals government, academia, defense sectors, well NGOs [1]. Threat intelligence units Microsoft, Amazon, CERT-UA published overlapping reports .
Phishing Attacks And Strategies To Mitigate Them V2 Steps To Take After Starting late October 2024, Russian state-sponsored threat actor Midnight Blizzard, known APT29 & Cozy Bear, been actively deploying sophisticated spear-phishing campaign targeting thousands individuals government, academia, defense sectors, well NGOs [1]. Threat intelligence units Microsoft, Amazon, CERT-UA published overlapping reports .
 Phishing Attacks And Strategies To Mitigate Them V2 About Evil Twin In post, we'll explore wiper attacks are, they work, cybersecurity strategies prevention, detection, mitigation. Wiper attacks defined. Wiper attacks a form malware engineered destroy corrupt data targeted systems. Wiper attacks unlike ransomware, encrypts data for
Phishing Attacks And Strategies To Mitigate Them V2 About Evil Twin In post, we'll explore wiper attacks are, they work, cybersecurity strategies prevention, detection, mitigation. Wiper attacks defined. Wiper attacks a form malware engineered destroy corrupt data targeted systems. Wiper attacks unlike ransomware, encrypts data for
 Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks
 Phishing Attacks And Strategies To Mitigate Them Powerpoint Phishing Attacks And Strategies To Mitigate Them Powerpoint
Phishing Attacks And Strategies To Mitigate Them Powerpoint Phishing Attacks And Strategies To Mitigate Them Powerpoint

